|
As a result, an organization's security and protection of its sensitive data is only as strong as its privileged credentials. To authenticate users and systems to privileged accounts, most organizations utilize a mix of privileged credentials such as passwords, API keys, certificates, tokens, and SSH keys. To maintain their security, all of these credentials must be securely stored, rotated, and additionally authenticated for each use with multifactor authentication (MFA). If left unsecured, attackers can easily obtain these valuable secrets and credentials, leading to the compromise of privileged accounts, the advancement of attacks, or the exfiltration of data. As organizations begin to focus on protecting passwords, attackers have shifted their attention to SSH keys, which are often overlooked. What is Privileged Access Management (PAM)?PAM is a set of processes and technologies used to manage and secure privileged access to sensitive resources within an organization. Privileged access refers to access to systems, applications, and data that is granted to users with elevated permissions or privileges, such as system administrators, network administrators, and database administrators. The primary goal of PAM is to ensure that only authorized users can access sensitive resources, and that those users are using their privileged access in a controlled and monitored manner. This is achieved through a range of security controls, including:
By implementing a PAM solution, organizations can reduce the risk of data breaches, compliance violations, and other security incidents that could result from unauthorized access or misuse of privileged accounts. The Difference Between IAM & PAMPrivileged Access Management (PAM) and Identity and Access Management (IAM) are both critical components of an organization's overall security posture. While there is some overlap between the two, there are also significant differences in their focus and capabilities. IAM is concerned with managing user access to resources based on their role within the organization. It includes processes and technologies that ensure users are authenticated, authorized, and granted appropriate access to systems and data based on their job responsibilities. IAM typically manages a large number of users with varying levels of access to different resources and applications. On the other hand, PAM is specifically focused on managing and securing privileged access to sensitive resources. This includes access to systems, applications, and data that are typically only granted to users with elevated privileges, such as system administrators, network administrators, and database administrators. PAM typically deals with a smaller number of users but is concerned with the highest level of access within an organization. The key difference between IAM and PAM is the level of access being managed. IAM focuses on managing user access to resources based on their role, while PAM is concerned with managing and securing privileged access to sensitive resources. Additionally, PAM typically involves more stringent security controls, such as session monitoring and recording, to ensure that privileged access is being used appropriately and not abused. Are IAM and PAM Complimentary?IAM and PAM are complementary solutions that work together to provide a comprehensive security framework for an organization. While there is some overlap in their capabilities, they address different aspects of security and access management. While there is some overlap in their capabilities, IAM and PAM address different levels of access and risks. IAM manages access to resources for all users, while PAM manages access to the highest level of access within an organization. Together, they provide a comprehensive security framework that ensures secure access management and control for all users, including those with elevated privileges. The Challenges of PAMImplementing an effective Privileged Access Management (PAM) program can be somewhat challenging, and organizations must be aware of the potential obstacles that they may face when implementing a PAM solution. Some of the common challenges include:
Overcoming resistance to change: Implementing a PAM program requires changes to existing processes and workflows, which can be met with resistance from users who are comfortable with the way things have been done in the past. It is essential to get buy-in from stakeholders and provide adequate training and support to ensure successful adoption. To address these challenges, organizations should carefully plan their PAM implementation and work with their vendors and stakeholders to ensure that all systems and applications are properly integrated and secured. It is important to establish clear policies and procedures for privileged access management and ensure that all users are trained on best practices for secure access management. Additionally, organizations should regularly assess their PAM solutions to ensure that they are effective and compliant with all regulatory requirements. Overall, implementing a successful PAM program requires a commitment to ongoing management and monitoring, as well as a willingness to adapt to changing security threats and compliance requirements.
0 Comments
Protecting against attacks in 5G networks is increasingly complex due to the disaggregation of network functions across the cloud. Telcos are essentially becoming cloud service companies, which is a necessary technology and business capability, but this increases the attack surface and opens up a multitude of new attack vectors as a result of leveraging common web protocols and APIs. The Telecoms Security Requirements (TSRs)The UK government’s Telecoms Supply Chain Review Report published in July 2019, highlighted the security risks as well as the economic opportunities associated with the next generation of telecommunications networks, particularly 5G and full fibre networks. Since the Review was published, the government has put this recommendation into action, developing a new security framework for providers of public electronic communications networks or services through the Telecommunications Security Act 2021 otherwise known as ‘the TSA’. The new telecoms security framework was developed in collaboration with the National Cyber Security Centre (NCSC), drawing on its technical expertise in cyber security matters relating to the telecoms sector. This Code of Practice provides guidance for large and medium‑sized public telecoms providers whose security is most crucial to the effective functioning of the UK’s telecoms critical national infrastructure (CNI). The 'technical guidance measures' specified in the Telecommunications Code of Practice, are broadly categorised as follows:
Our focus in this article is primarily on the virtualisation layer in the form of Telco Cloud, but before we get into some of the strategies that will help to secure this cloud infrastructure, lets take a closer look at what it actually is. An Overview of Telco CloudThis is an industry term used to describe the private cloud infrastructure upon which 5G is built and significantly changes how the network is operated. Telco Cloud is not something that you can buy off the shelf – it’s not a single product or technology, but a collection of cloud technologies including compute, storage, networks, orchestration and so on. As the name suggests, the Telco Cloud is focused on the implementation, standardisation, and use of cloud technologies specifically in Telco environments. This reliance on cloud technology provides significant advantages:
These are great benefits, but as mentioned, it does increase the attack surface and opens up a multitude of new attack vectors. However, this is nothing new in the world of cloud computing. Indeed, cloud security architecture has been tried and tested over many years with a multitude of security controls. These are not new ideas, they are just new to the telecoms industry. This is good news as the heavy lifting has already been done in other industries such as finance, retail, manufacturing and so on, that have been embracing digital transformation for years. So cloud technologies of any flavour, whether that is public cloud, private cloud, hybrid cloud or telco cloud, all have security risks. It goes with the territory and that risk has to be managed. To secure 5G networks, your most important preparation revolves around design and implementation choices for new technologies, including virtualisation, containerisation, and orchestration. As mentioned, these technology capabilities, while new to telecom networks, are well-proven in other industries. We can learn from this, and apply this to the telecoms world - specifically, to the Telco Cloud. In the next section, we’ll take a closer look at how we can mitigate many of the cyber security risks in the Telco Cloud. Threat Mitigation StrategiesThe aim of these controls is to mitigate risk to an acceptable level. In this article, we'll be taking a look at the following areas and controls, but this is by no means an exhaustive list:
Where to Start?Prior to deploying the telco cloud, the organisational security policy needs to be updated to incorporate the specific requirements of telco cloud in terms of people, process and technology that is consistent with any regulatory or legal requirements for the organisation. In the case of the telecoms industry in the UK, we have the Telecommunications Security Act 2021 and the Telecoms Security Requirements and there are some specific milestones for compliance as we discussed in the previous article. Overall, the security policy spells out the rules, expectations, and overall approach that an organisation uses to maintain confidentiality, integrity, availability, authenticity, and non-repudiation of it's data. Supply Chain Security5G networks depend on a vast and distributed supply chain that includes hardware, software and services. Lets take hardware as an example, and in this scenario, a server, because all software packages, whether they are virtualised or containerised, are hosted on some type of server hardware. Components are sourced from many vendors, that may be distributed around the world, and then brought together in a factory, where the server is assembled. From here the server is tested, then packaged and shipped. It may go through customs and then onward to distributors until it is finally delivered to the customer site, perhaps a data centre in a telecoms company. As we can see, the server hardware passes through a number of touchpoints in its journey to the customer and we need to ensure that the server has not been tampered with in any way during that journey. We need to ensure the integrity of the server hardware. This is the essence of a secure supply chain. There are many initiatives that help to secure the supply chain and indeed, vendors may well implement their own version of a secure supply chain. An example of one feature that can be implemented to increase security in the supply chain, specific to this example of a server, is Secure Boot. This is a security standard developed by members of the computer industry to help make sure that a device boots using only software that is trusted by the Original Equipment Manufacturer (OEM). We’ll discuss this later in the article. Secure Multi-TenancyA fundamental concept of telco cloud is that of the tenant. A tenant is a logically isolated construct representing a customer, department or network function or service used to deploy workloads. Multi-tenant Telcos must ensure that each tenant is fully secure from attacks, breaches, or insecure communications from other tenants. The Telco Cloud infrastructure can be configured into a secure multi-tenant environment across network functions through the following means:
Many of the features of micro-segmentation, identity and access management, role-based access etc are dependent on the vendor solution being implemented but we'll take a closer look at the architecture and principles in this article. Zero Trust Architecture
Authentication and authorisation for both users and devices are discrete functions performed before a session to a specific resource is established. Essentially, zero trust focuses on protecting resources (assets, services, workflows, network accounts, etc.), not network segments, as the network location is no longer seen as the prime component to the security posture of the resource. Zero trust involves the following principles:
Many of the security controls discussed below are components of the Zero Trust Architecture. Identity and Access ManagementIdentity and access management (IAM) is the practice of making sure that users or services have the right level of access to resources such as systems, applications, network resources etc. User roles and access privileges are defined and managed through an IAM system. When granting system access to individuals, we need to apply the principle of least privilege, and only grant a user the system privileges they actually need to complete their tasks. Identity services support Role Based Access Control (RBAC), where users belong to specific group based on their role. Identity services reference the roles of the user attempting to access a particular service and will take into consideration the policy rule associated with each resource then the user’s group/roles and association to determine if access is allowed to the requested resource. Privileged Access ManagementPrivileged credentials serve as the keys to an organization's IT kingdom, providing access to sensitive data and critical systems. However, these credentials are highly sought-after by external attackers and malicious insiders who attempt to gain direct access to the heart of the enterprise. As a result, an organization's security and protection of its sensitive data is only as strong as its privileged credentials. To authenticate users and systems to privileged accounts, most organizations utilize a mix of privileged credentials such as passwords, API keys, certificates, tokens, and SSH keys. To maintain their security, all of these credentials must be securely stored, rotated, and additionally authenticated for each use with multifactor authentication (MFA). If left unsecured, attackers can easily obtain these valuable secrets and credentials, leading to the compromise of privileged accounts, the advancement of attacks, or the exfiltration of data. Privileged Access Management (PAM) is a set of processes and technologies used to manage and secure privileged access to sensitive resources within an organization. Privileged access refers to access to systems, applications, and data that is granted to users with elevated permissions or privileges, such as system administrators, network administrators, and database administrators. The primary goal of PAM is to ensure that only authorized users can access sensitive resources, and that those users are using their privileged access in a controlled and monitored manner. Network Micro-SegmentationSegmentation in cloud-native networks is easier because software-defined networks allow any granularity of segmentation through configuration, and can flexibly be adopted to evolving functional requirements. Firewalls are also important as they provide another layer of technical control. It is also harder to implement because new connections between network elements arise from virtualisation and/or containerisation whereas in earlier network generations, the only connection between elements was a network cable. Today, different network functions typically reside as containers in the same cluster and the velocity and volume of CNF updates on the 5G network have increased significantly and are more complex due to the disaggregation. For segmentation to be effective in a containerised deployment, the CNFs need the appropriate security configuration to prevent hackers from being able to escape to other containers and the underlying infrastructure. As mentioned, virtual firewalls can be combined with micro-segmentation and dynamic security policies to separate and protect all types of network traffic, virtual machines, containerised applications, and workloads. The ability to segment the network in this way, restricts the lateral movement in the event of a breach. Protecting the Management PlaneProtecting the management plane of the virtualisation layer is critical and this is a big focus of the Telecoms Security Requirements (TSRs) we discussed in the previous article. We need to design the architecture so that the management elements, including the administrative network and the VIM, can be isolated from other aspects of the virtual infrastructure. Management plane components, such as the Virtualised Infrastructure Manager (VIM) can reside in a trusted segment or security zone that is segmented from the virtualisation layer. Virtual firewalls, micro-segmentation, and security groups protect the trusted domain. The management interfaces use secure, encrypted channels to administer virtual network functions or VNFs, the VMs and the hypervisor. Advanced security policies and rules can be applied at the virtualisation layer boundary to further control access to the management plane. Orchestration and Automation LayerTelco cloud orchestration and automation is important for efficient NFV lifecycle management, including onboarding, instantiation, configuration, scaling, updating, healing and monitoring. However, this also introduces an expanded attack surface to exploit vulnerabilities from improper isolation, insecure API implementation that leads to risks such as unauthorised user and function-level access, excessive data exposure, and broken object level, or indeed any of the top 10 API vulnerabilities identified by OWASP. Several steps can be taken to mitigate risks in orchestration and automation, including:
Infrastructure HardeningThis typically involves disabling all unused services and ports, changing default root passwords and so on. For example, some servers have a chipset that acts as a silicon root of trust and includes an encrypted hash embedded in the silicon hardware at the chip fabrication facility. The hardware determines whether to run the firmware and does so only if it matches the encryption hash that is permanently stored in the chipset silicon. Some server hardware vendors embed the validation signatures in the ASIC, which means that they are burned into the ASIC and therefore the silicon root of trust protects the server from any firmware attacks all the way through production, shipping, distribution, and the entire supply chain process. As mentioned earlier, a feature called Secure Boot ensures that a device boots using only software that is trusted by the Original Equipment Manufacturer (OEM). Secure boot leverages the chain of trust rooted in the silicon root of trust to ensure that every component in the boot chain is trusted. Secure boot is intended to prevent boot-sector malware or kernel code injection. It ensures that each component launched during the boot process is digitally signed and that the signature is validated against a set of trusted certificates loaded in the UEFI BIOS. Unified Extensible Firmware Interface (UEFI) is a specification for a software program that connects a computer's firmware to its operating system (OS). UEFI is expected to eventually replace basic input/output system (BIOS) but is compatible with it. PatchingYour operating procedures should incorporate a process for learning about new vulnerabilities and security updates. Hardware and software vendors typically announce the existence of vulnerabilities, and could offer workarounds and patches to address these. Regular patching and hardening remain critical in shortening the time window during which network elements are exploitable through newly discovered security vulnerabilities. Cloud-native 5G makes patching both easier and harder compared to earlier network generations. Easier, because network elements can be rebuilt on the fly through an automated CI/CD pipeline, each time including the latest patches and configuration settings. Harder, because virtually all patching must be done through these automated processes due to the larger scale and complexity of 5G compared to earlier generations. For cloud-native networks, it is best practice to maintain “golden” master images with the latest patches and configuration settings, and to base all containers on these images. A packer automatically builds network elements by combining a golden image with element-specific software, and stores the images in a repository. Automated deployment processes use these artifacts to deploy any number of required network elements, each including the latest security baseline. Firmware UpdatesPhysical servers use complex firmware to enable and operate server hardware and lights-out management cards, which can have their own security vulnerabilities, potentially allowing system access and interruption. To address these, hardware vendors will issue firmware updates, which are installed separately from operating system updates. You will need an operational security process that retrieves, tests, and implements these updates on a regular schedule, noting that firmware updates often require a reboot of physical hosts to become effective. Node and Workload AttestationThis is a means of certifying the identity of a server or workload against a central attestation authority. The unique identifier for the server could be an identity that is immutable and burned into the hardware, such as a hardware root of trust or trusted platform module. Node attestation can help in remote boot attestation for cloud workloads such as is provided by the CNCF Keylime project. Remote boot attestation can prevent a virtual machine from booting if the underlying server is not attested. In addition, the integrity of workloads can be continuously monitored using the Linux Integrity Measurement Architecture (IMA). The workload attestation can be revoked if the IMA indicates that the workload signature has changed from what has been registered in the framework. An attested server is trusted and can be allowed to run authorised workloads. But how can workloads that are provided by different vendors, and running on different hardware platforms trust each other? Workload attestation allows software entities interacting in complex service-based architectures to each have a unique, verifiable identity; and to use this identity to be able to trust one another. The CNCF SPIFFE/SPIRE framework is one that enables this trust mechanism. Node attestation helps in mitigating the risk of rogue elements being introduced into the network and the threats arising from running workloads obtained from many different vendors on the telco infrastructure. Node and workload attestation helps in mitigating against Day 0 threats. If all new hardware and software elements that are to be introduced into a data centre are meticulously fingerprinted before being deployed, there is little opportunity for rogue hardware or software to be introduced. Network AttestationThe IEEE 802.1X standard is one such mechanism that provides port based network access control at Layer 2. The authenticator is a process on the switch that blocks the connected port until the server or workload (known as the supplicant) authenticates via an exchange of keys. Network attestation helps in mitigating the risk of rogue elements being introduced into the network and the threats arising from running workloads obtained from many different vendors on the telco infrastructure. Encryption at Rest
Storage device encryption requires that all data being written to the device be encrypted with a secret key and decrypted while being read. Encryption of storage devices offers several benefits:
There are several types of mechanisms by which encryption can be enforced: Software-based encryption The encryption and decryption are performed by a software layer before writing and after reading data from a storage device. Hardware-based encryption In the case of hardware-based encryption, the encryption and decryption are performed by a dedicated hardware device before writing and after reading data. Encryption in TransitSecure methods of communication over a network are becoming increasingly important and in many cases, mandated. Encryption is typically used to provide additional confidentiality and integrity of data as it transits a network. Traffic in the Telco Cloud is encrypted in transit using Transport Layer Security (TLS) with an industry-standard Advanced Encryption Standard (AES) cipher. TLS is a set of industry-standard cryptographic protocols used for encrypting information that is exchanged over the network. AES-256 is a 256-bit encryption cipher used for data transmission in TLS. The UK NCSC provide guidance on encryption of data in transit which states that you should be sufficiently confident that:
TLS versions 1.3 and 1.2 are the recommended versions for deployment. TLS versions 1.1 and 1.0 have been formally deprecated by the IETF. TLS 1.3 introduced some major changes in that it uses different cipher suite definitions to earlier TLS versions, and has different configuration options. Secure Inter-NF CommunicationsFor secure inter-NF (Network Function) communications within the 5G core, Service Based Architecture defined by 3GPP specifies authentication, authorisation, and encryption of API calls between the 5G core Network Functions. The authentication and transport security using encryption can be provided by TLS 1.2 or 1.3 as discussed above. Token-based authorisation using OAuth 2.0 can be used for authorisation of NFs. 3GPP has also taken steps in enhancing the security for the external API communication by introducing security features and security mechanisms for the common API framework (CAPIF). Security Information and Event ManagementSIEM systems have the advantage of a library of ready made rules that are tuned to detect different types of attacks; they also come with features such as compliance and audit reports that can help with regulatory reporting. Consideration should be given to integrating an operations management suite for monitoring and remediation of the NFVI and VNFs. The platform should provide continuous, context-aware visibility over service provisioning, workload migrations, auto-scaling, elastic networking, and network-sliced multi-tenancy across VNFs, hosts, clusters, and sites. Alerts can flag configuration and compliance gaps and security vulnerabilities. The management suite can profile and monitor traffic segments, types, and destinations to recommend security rules and policies for traffic. It can also identify violations of security policies or vulnerable configurations and traffic routes. CNF SecurityWhilst containerisation has many benefits, it does come with some challenges including:
When deploying containerised network functions (CNFs), we need to consider how to secure the container lifecycle. This involves securing the CNFs as they move through the CI/CD pipeline and we’ll discuss this in more detail in a future article on DevSecOps, however, in the meantime, here are a few points to consider:
ConclusionWe've covered a lot of ground in this article but this isn't an exhaustive list of threat mitigation strategies and controls for Telco Cloud. There is a lot more to discuss! Indeed, we have primarily focused on administrative and technical security controls, however, there are many other considerations in the broader security architecture. What is clear is that security is intrinsic to the Telco Cloud. It should be secure by design and integrated in every layer of the architecture so that security is programmable, automated and context aware.
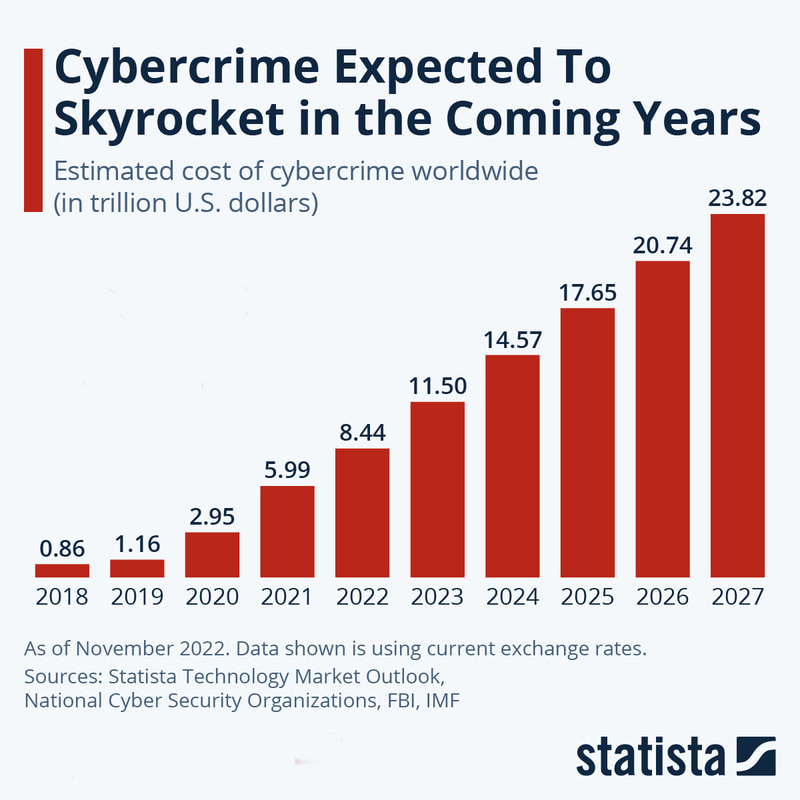
The security and resilience of the UK’s telecoms networks is of paramount importance. Telecoms networks are central to the way we live and work, they enable us to do business, keep in touch and access a vast range of services across the digital economy. However, the security risks and requirements are shifting as telecoms providers or Telcos transition to 5G networks. 5G uses software-defined networks and virtualises many of its most fundamental components across the core and the radio access networks. This creates new market opportunities but also creates new attack vectors for hackers to exploit. Indeed, cybercriminals have come to view attacks on critical infrastructure as a lucrative target. Any attack that causes service disruption in our critical national infrastructure can potentially have enormous repercussions on national security and the economy. There is also a knock-on effect in that many other critical services and providers such as power and water suppliers rely heavily on telecoms services and would therefore be affected by any outages. This raises many concerns about the security of our critical national infrastructure. Disaggregation of FunctionsProtecting against attacks in 5G networks is increasingly complex due to the disaggregation of network functions across the cloud. Telcos are essentially becoming cloud service companies, which is a necessary technology and business capability, but this increases the attack surface and opens up a multitude of new attack vectors as a result of leveraging common web protocols and APIs. In addition, network slicing will become more mainstream, allowing for multiple specialised software-defined networks to be hosted on the same network infrastructure. However, each slice will require its own specific security controls to be implemented adding to the complexity. Cost of Cybercrime
One recent report revealed that in Q3-2022, the Telco sector was the target of over 43% of all DDoS attacks. This report shows that the number of attacks in the telecoms sector grew by a factor of 7 since Q3 2021. Most of the attacks on telecoms were carried out with the aim of extortion and blackmail. Government Regulation & Compliance
The government’s UK Telecoms Supply Chain Review Report published in July 2019, highlighted the security risks as well as the economic opportunities associated with the next generation of telecommunications networks, particularly 5G and full fibre networks. Since the Review was published, the government has put this recommendation into action, developing a new security framework for providers of public electronic communications networks or services through the Telecommunications Security Act 2021 otherwise known as ‘the TSA’. The new telecoms security framework was developed in collaboration with the National Cyber Security Centre (NCSC), drawing on its technical expertise in cybersecurity matters relating to the telecoms sector. This code of practice provides guidance for large and medium‑sized public telecoms providers whose security is most crucial to the effective functioning of the UK’s telecoms critical national infrastructure (CNI). The framework established through the TSA comprises three layers:
To ensure security risks are mitigated proportionately, the code of practice includes a tiering system which sets out the different expectations on public telecoms providers. The tiering system places public telecoms providers in one of three tiers, based on their commercial scale:
Ofcom's Remit
Ofcom also has the ability to direct telecoms providers to take interim steps to address security gaps during the enforcement process. In addition, in cases of non‑compliance, including where a provider has not complied with a notification of contravention, Ofcom can issue financial penalties. The amount of a penalty is specified as what the Secretary of State determines to be:-
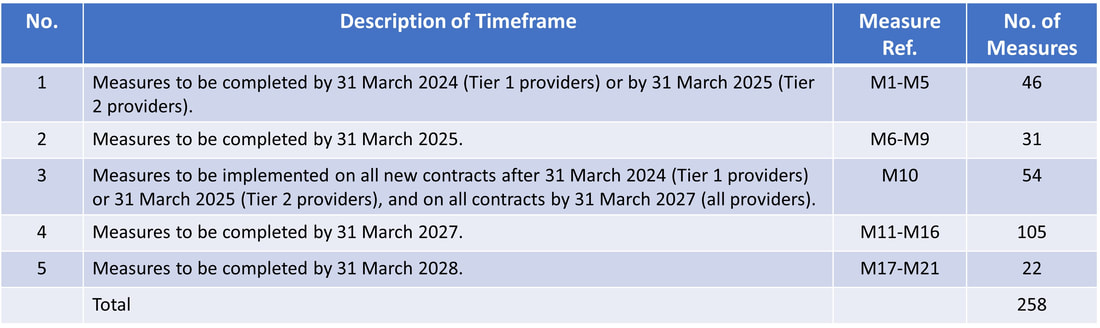
The penalties can be significant but may not exceed 10 per cent of the turnover of the public communications provider’s relevant business for the relevant period, and may not exceed £100,000 per day. This is certainly an incentive to get this right! Timeframes for ComplianceThe telecoms security framework came into force on 1 October 2022, however, it would not have been realistic to expect public telecoms providers to have met all their obligations from that date. Instead, specific recommended compliance timeframes, by which providers are expected to have taken relevant measures have been set out in the code of practice. It is also recognised that it would not be appropriate, proportionate, or technically feasible, to expect providers to implement all measures at the same time. The timeframes specified in the code of practice reflect which guidance measures are most important and/or most straightforward to implement first, and which guidance measures may require more time to implement. There has been a delay on the earliest implementation date for some security measures which changed from 31 March 2023, to 31 March 2024, for ‘the most straightforward and least resource intensive measures’ giving Telcos a further year. Other deadlines, for 'more complex' security measures, remain unchanged at 31 March 2025, 2027 and 2028 for Tier 1 and 2 providers, with longer for Tier 3 operators. Indeed, this leaves a lot of room for interpretation. Whilst the specific definition of the least, relatively low, most complex and most resource-intensive measures remains up for debate, it will most likely involve a lot of work to achieve compliance with these new regulations. What Does this Mean for Telcos?
‘anything that compromises the availability, performance, functionality or confidentiality of the network, allows unauthorised access or interference, or causes signals or data to be lost or altered without the provider’s permission’. On the face of it, this doesn’t sound too daunting or burdensome. However, if we dig a bit deeper, we get a much more detailed picture of what is required for compliance. This includes the following areas, but there is a lot more detail in each of these domains. Network architecture - provides guidance on the design, implementation and management of secure networks. The architectural and design decisions which are made when creating and modifying a provider’s network or supporting systems are critical to the security of that network. This security architecture determines how difficult it will be to compromise or disrupt the network, the scale of any associated impact, and whether the provider is likely to detect and recover from any compromise. Protection of data and network functions - provides guidance on the measures to be taken to protect data and network functions that could be at risk of security compromises. Protection of certain tools enabling monitoring or analysis - provides guidance on the measures to be taken to protect the tools that enable the monitoring or analysis in real time of the use of the network or service, or the monitoring or analysis of the content of signals. Monitoring and analysis - provides guidance on the measures to monitor and analyse the use of their networks in order to identify any security compromises. While not directly a set of preventative controls, security monitoring fundamentally underpins the security posture of a network or system. Supply chain - provides guidance on the measures to identify and reduce the security risk arising from actions taken or not taken by third party suppliers. Prevention of unauthorised access or interference - provides guidance on the measures to be taken to prevent the occurrence of security compromises that consist of unauthorised access to networks or services. Preparing for remediation and recovery - provides guidance to prepare for the occurrence of security compromises with a view to limiting the adverse effects of security compromises and being able to recover from them. Governance - provides guidance on the measures to ensure appropriate and proportionate management of the persons who are given security‑related tasks. This is intended to ensure that providers employ the appropriate security governance and business processes to protect UK networks and services. Reviews - provides guidance on the measures to ensure that regular reviews of their security measures are undertaken. Patching and updates - provides guidance on the measures to be taken to deploy patches or mitigations (including software updates and equipment replacement) as well as the necessary security updates and equipment upgrades. Competency - provides guidance on the measures to be taken to ensure that the persons who have been given security‑related tasks can conduct their duties appropriately. Testing - provides guidance on the measures to be taken to carry out appropriate tests. The purpose of testing, or ‘red team’ exercising, is to verify the security defences of the network, and identify any security weaknesses prior to any potential attacks. For this reason it is essential that the testing simulates, so far as possible, real world attacks. Assistance - provides guidance on the measures to be taken to reduce the risk of security compromise by seeking and providing appropriate assistance. In certain circumstances it is appropriate for providers to receive information from other providers that would help to reduce the risk of security compromises occurring. Technical Guidance MeasuresWithin each of the domains listed above, there are specific technical measures to be taken by providers, grouped by the date by which they are expected to be completed. In total, there are 258 technical measures, however, due to the amount of detail, we cannot cover them here, but we'll circle back to these in future articles. As we can see in the table below, these timeframes are divided into 5 phases with the first deadline of 31st March 2024 applying only to Tier 1 providers. Across these phases, there are a number of groupings as follows:
However, it should be noted that the extent to which each technical guidance measure can contribute to ensuring compliance with any specific regulation will depend on the facts of each case. So clearly, it is not a straightforward, tick- in-the-box exercise, and once again, there is room for a certain degree of interpretation. Where to Start?Start at the beginning. Telcos should get an understanding of their current state and begin testing and auditing their existing security infrastructure and staff’s cyber awareness. This will serve two purposes:
Telcos can also start to identify which of the regulations fall into the different timescales. While the complexity of each security task may vary for different providers, depending on their existing network and the tools being used, identifying quick wins that are easy to achieve, will help to prepare for the first deadline. Following this, map out the dates needed to achieve compliance with all of the other TSRs. ConclusionFor all of 5G’s transformative potential, the risks are high. Hackers will exploit everything, everyone, everywhere they can reach. Whilst threats are escalating and the challenges in protecting these networks are rapidly evolving, with a multi-layered defence that focuses on protecting access to key assets and systems, based on the guidance we have discussed above, Telcos can significantly bolster the security posture of their network infrastructure.
Though the Government’s deadline (31st of March 2028) for full compliance may seem quite a way off in the future, Telcos should begin to take action now. While compliance with the TSR's may look like a cause for concern in terms of the potential for complex, resource intensive work streams, it is actually a good thing. This is because these measures are necessary for the security of the communications infrastructure. These networks have become critically important in our lives and as we see the deployment of more advanced 5G infrastructure, (ORAN, 5G Standalone, Network Slicing) with more functions and capabilities disaggregated across the cloud, the more important network security becomes. Therefore, we need to ensure they are protected, without underestimating the effect a security breach could have on all of us. |
AuthorTim Hardwick is a Strategy & Transformation Consultant specialising in Technology Strategy & Enterprise Architecture Archives
April 2023
Categories
All
|
Site powered by Weebly. Managed by iPage